The latest automatic triage engine "SSVC" is installed.
Need for ongoing vulnerability management and rapid response.
Exploitation of publicly disclosed vulnerabilities ranked 6th among the top 10 information security threats.
- In the"Information Security 10 Major Threats 2022"published by the Information-technology Promotion Agency, of Japan (IPA), "Increased exploitation of vulnerability countermeasure information as it becomes publicly available" is ranked 6th (10th in FY2021), and it is now essential for companies to manage vulnerabilities on a daily basis.
Inadequate vulnerability response poses a major risk to management.
- If a dangerous vulnerability is left unchecked and exploited, possible damage could include an attacker executing arbitrary code on a Web server from the Internet, bypassing authentication, gaining free control of the server from the Internet, leaking information, or using the server as a stepping stone. This is a risk that can have a significant impact on business management, such as inconveniencing customers and business partners. In particular, the following dangerous vulnerabilities, which are actively being exploited, must be promptly addressed.
Configuration management and quick response required.
- According to "Information Security White Paper 2022" published by IPA, it is stated that advance preparation is necessary to respond steadily and without delay when new vulnerabilities are disclosed.
- Appropriate configuration management of systems owned or used.
- Routinely collection of vulnerability information on software and other components of the system.
- We also recommend the following procedures for measures that should be established in advance.
- Methods of collecting vulnerability information on software and other software used.
- How to respond if a vulnerability is identified.
- Priority of response based on the urgency and severity of the vulnerability.
- Criteria for whether or not to contact other departments, vendors, etc..
- The third item in the above recommendation states "Priority of response based on the urgency and severity of the vulnerability" but the difficulty of determining priority is high and poses challenges with conventional methods.
Issues with traditional vulnerability triage methods.
Score-based triage challenges.
- Each disclosed vulnerability is assigned a CVSS score, a numerical value ranging in severity from 0-10.
- The operation could be judged based on this score, but there are some issues as follows.
- CVSS is information about the vulnerability itself and cannot be determined on an "Actual risk basis".
- No proper assessment is done for the system environment and attack conditions
- No guidelines are provided for decision making.
- Ideally, "the Actual risk" = "Vulnerability" x "Threat" x "Asset Value/Business Impact" should be considered when making response decisions, rather than score-based decisions when actually operating the system.
Risk-based decisions require expertise and significant human costs.
- To determine the priority of a detected vulnerability in the relevant system by "actual risk" = "vulnerability" x "threat" x "asset value/business impact", the following conditions, which vary depending on the system environment and the situation at that time, are comprehensively considered.
- Abuse-level.
For example, the risk of being attacked differs between vulnerabilities that are actually used for attacks in the real world that fall under CISA-KEVC, a list of vulnerabilities that require caution as selected by U.S. Cyber Security, and vulnerabilities for which the PoC has not yet been released. The level of actual exploitation should be considered when determining priority. - External Exposure to the Internet.
Systems exposed to the Internet are subject to attack from all over the world and require urgent action, while internal systems and other systems that cannot be accessed from the Internet are attacked only from a limited number of pathways.Attack pathways must be considered in determining priority. - A vulnerability that is easy for attackers to use?
Vulnerabilities such as RCEs, which allow arbitrary code to be executed remotely over a network, are attractive to attackers because they are easy to make controllable from the outside after intrusion. Such vulnerabilities should be addressed as a priority. - Business-impact.
A mission-critical system exposed on the internet that would shut down a company's business activities if attacked and attendance management system in the company network have different priorities for response, even if the vulnerabilities are the same. Each system must be determined on a system-by-system basis, taking into account its business impact.
- These decisions require technical knowledge, and in terms of volume, the human cost of dealing with more than 20,000 vulnerabilities disclosed annually on a daily basis without delay would be very high.
SSVC to solve the challenges of traditional score-based triage methods.
What is SSVC - Carnegie Mellon University's latest framework for vulnerability response
A vulnerability management framework designed to address the above CVSS challenges is the Carnegie Mellon University paper "SSVC" (Stakeholder-Specific Vulnerability Categorization). SSVC derives "Actual risk" by tracing a decision tree based not only on vulnerability information but also on the "four variables" shown in the figure below, and classifies response priorities into four levels: "Immediate," "Out-of-cycle," "Scheduled," and "Defer".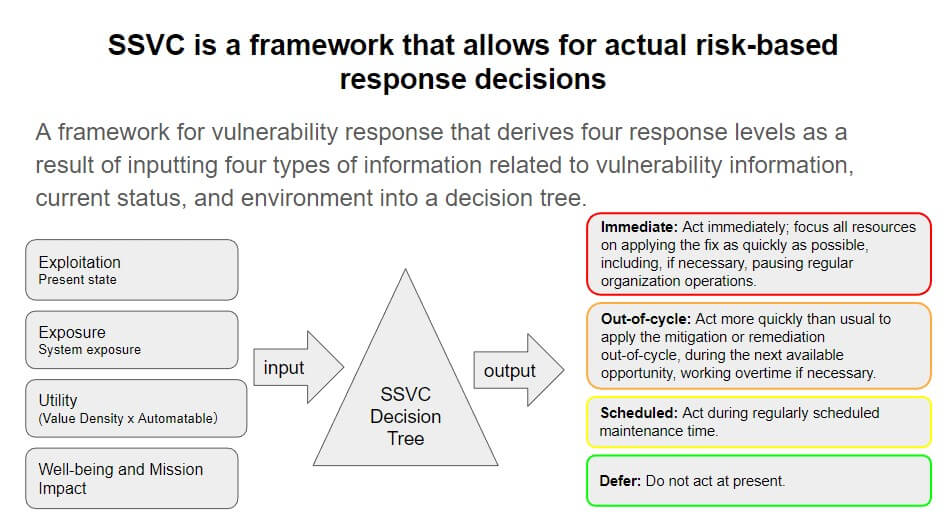
The latest automated triage engine, “SSVC”, is installed. Fully automated from risk-based decision making to response instructions.
FutureVuls built-in SSVC engine classifies vulnerabilities detected into 4 priority levels
- FutureVuls built-in SSVC engine automatically classifies response priorities on an actual risk basis on behalf of experts, considering the following environment and current conditions.
- Vulnerability Exploitation Status.
- External exposure of the system to the Internet.
- The value of using vulnerabilities from an attacker's point of view.
- The business impact of the system in the event of an attack.
SSVC's performance in determining priority is "15 times better" than score-based.
- We measured the number of cases classified in two ways, by SSVC and CVSS scores, in an environment that assumes a mission-critical system published on the Internet.
- Out of 4,716 system-wide vulnerabilities detected.
- When categorized by SSVC, there are "16" Immediate cases that require an immediate response and "50" Out-of-cycle cases that require an unplanned response.
- CVSS score-based (7.0 or higher) classification: "2,863" (about 43 times more than SSVC).
- "990" on a CVSS score basis (8.0 or higher) (about 15 times more than SSVC).
- Thus, SSVC was able to narrow down the number of vulnerabilities requiring "Immediate response" and "Unplanned response" to a realistic number that could be addressed.
- Please refer to "Tutorial > Automatic Triage" for a more detailed description.
Automatic triage based on SSVC decision tree derivation results.
- The results derived from SSVC can be used to trigger the automatic setting of task priorities, deadlines, and statuses.
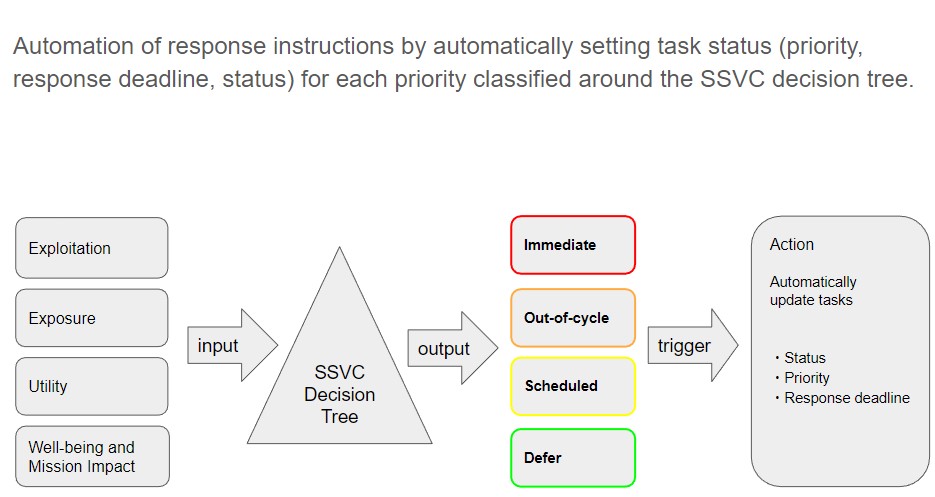
- For example, a task that is "Immediate" (requires immediate attention) can be set to "High" priority and task due date in two weeks, while a task that is "Scheduled" (to be handled at the next scheduled maintenance) can be set to "Defer" (pending) status and "Low" priority, and task due date can also be scheduled, for example, on the Wednesday of the second week of December, the next maintenance day.
Daily response is only required for automatically triaged critical vulnerability diffs.
- The operator is supposed to respond to the tasks determined to "Immediate" and "Out-of-cycle" by SSVC and automatically assigned to "Significant unaddressed" on a daily basis with a differential.
Clearly understand the basis for the decision.
- SSVC derives priority by pursuing the decision tree, so the basis for decisions is clear.
- For example, if an organization is operating on a score basis with a rule of responding to "8.0 or higher" in the traditional way, the debate such as "8.0 and above are dangerous, but are the vulnerabilities in 7.9 safe?" is endless. SSVC uses a decision tree to make clear decisions.

Detailed Information
- For more information about SSVC and the automated triage of FutureVuls, please see below. Also, if you would like a demo or more information, please request an online information session by clicking on "Contact Us" at the top of the page.
- Tutorial > Automated Triage


