Support vulnerability management for operations personnel
Setup
Registration of the target system is completed with a single command line
- Easy setup from scanner installation to OS (for LinuxOS/WindowsOS) vulnerability detection with a one-liner.
- The scanner is a single binary, making it easy to combine with other tools such as Ansible.
System availability comes first. We can't put any extra load on the system.
- Registration for various environments, such as closed network scanning or library scanning, can be set up in minutes.
- Network devices can be registered on the screen. No installation or network access to the actual device is required.
Can be introduced with little impact on existing systems
- It is a low-load scanner that acquires package information and memory information. In addition, because of its scheduled execution (cron/task scheduler), there is no agent that is always running, and scheduled execution is possible in accordance with business hours.
- Since no pseudo-attacks such as network scanners are performed, there is no impact on services.
- It works by simply deploying a single file of statically linked binaries. No additional dependency packages are required.
- It is also possible to perform agent-less remote scanning using SSH from the same network without inserting binaries into the server to be scanned.
Full security measures
- Security measures such as MFA, source IP address restrictions, password list attack countermeasures, and unauthorized login detection are implemented.
- It works by allowing HTTPS from the customer system side to the FutureVuls service side. There is no communication from the service to the customer system.
Information Gathering
Cloud, on-premise, and closed network environments, all managed from a single view
- Vulnerability detection in multi-cloud, on-premise, and closed network environments is also supported.
- No need to use different tools for different environments, with FutureVuls you can manage all your environments in one view.
Manage only vulnerabilities that are relevant to your system
- You don't need to see all of the more than 15,000 vulnerabilities that are published annually; FutureVuls allows you to manage your response status only for those vulnerabilities that are relevant to your system.
Real-time understanding of vulnerability risk changes
- You will be notified with vulnerability information updates, such as changes in CVSS scores and severity, and the release of attack code, so you can review your risk assessment and response based on the latest information.
Impact Study/Information Sharing and Decision Making
Prioritize high-risk vulnerabilities that are automatically sorted and addressed
- A severity filter function is available to automatically assign severity to detected vulnerabilities based on pre-defined criteria such as CVSS vectors and external status of the vulnerability.
- When a vulnerability is detected that meets the conditions of a predefined critical filter, multiple members can use the same filter rules to make decisions and respond in a prioritized manner.
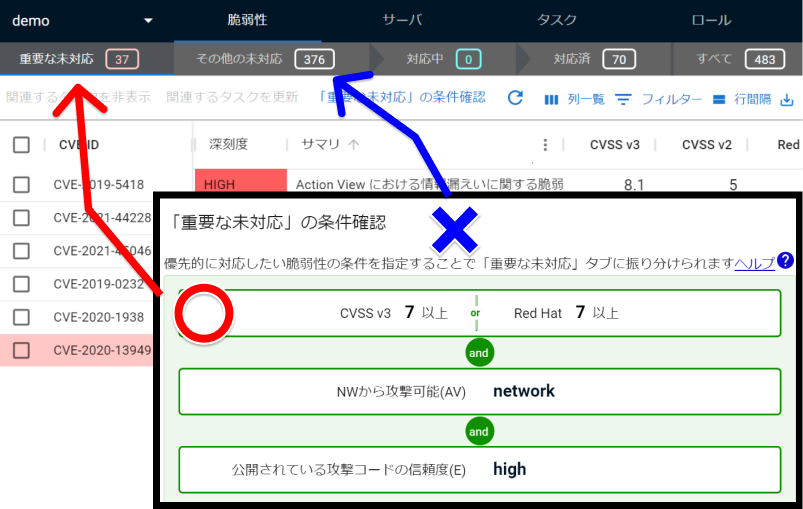
Consideration of response policy based on additional information for risk mitigation
- The availability of software updates, mitigation and workaround methods, and IPS protection rules are displayed on the screen. You can take action while viewing the system status.
Response and management
Task management of responses to detected vulnerabilities
When a vulnerability is detected, the report is automatically generated as a task of "1 server x 1 vulnerability".
Tasks that are raised are managed with the following status according to the status of response. The task will be automatically closed when the vulnerability is resolved.
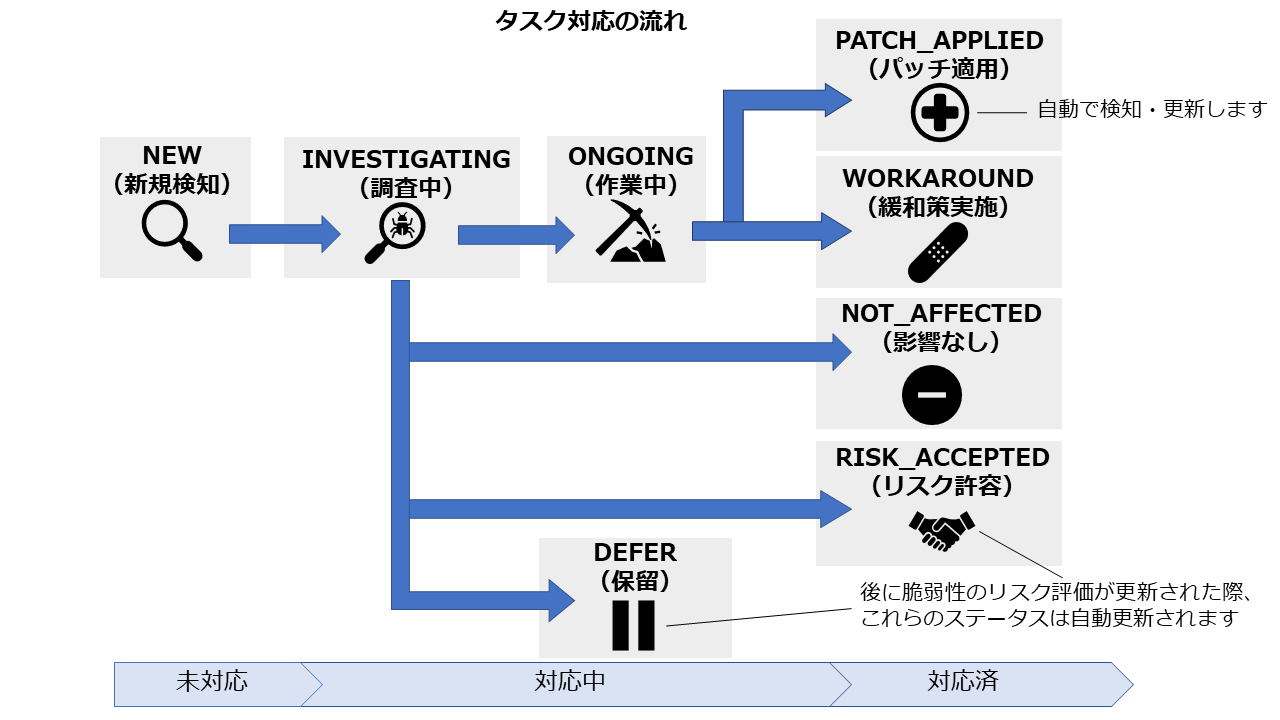
Support for software update methods tailored to your environment
- Displays commands for updating the server to resolve the vulnerability. The operator executes the command displayed on the screen on the target server to resolve the vulnerability.
- The Ansible Playbook, which can be downloaded from the screen, can be used to automate the update process.
- AWS integration Once configured, OS packages can be updated via AWS Systems Manager from the FutureVuls screen.
Automatic application of protection rules in conjunction with IPS
- When configured in conjunction with Trend Micro Cloud One Workload Security ("Workload Security"), it automatically generates defense rules optimized for detection results.
- If the detected vulnerability is actually being protected by Workload Security, the task status is automatically set to "WORKAROUND (mitigation in progress)".
- You can see on the FutureVuls screen "when a defense rule exists but is not enabled," so you can notice when a defense rule is not being applied.